Become passwordless in Azure AD
Passwordless authentication is a form of multifactor authentication that replaces the password with a secure alternative. As the name implies it is not necessary to enter a password anymore while authentication against Microsoft 365/Azure AD.

The background
Password authentication have been around for more than 60 years and have never very been user friendly. The first computer password was developed in 1961 at MIT (Massachusetts Institute of Technology), for Compatible Time-Sharing System (CTSS). CTSS was designed with multiple users accessing the computer at once through a console and this presented a challenge on how to protect each session and make them private.
“Putting a password on for each individual user as a lock seemed like a very straightforward solution.” -Fernando Corbató head of the CTSS program
Fast forward time to today, 80% of hacking-related breaches involves either stolen or weak passwords that were easily guessed by the cybercriminals. Most users do not set different passwords on each website/system but use the same (weak) password again and again.
Trying to mitigate this issue, engineers came-up with multi-factor authentication which is additional key beside the username and password combination. Adding a second factor to your authentication reduces the probability of account compromise by 99.9%, but impacts the user experience heavily.
Microsoft have been pushing a new technology called “passwordless authentication” for Azure AD. Passwordless authentication is a form of multifactor authentication that replaces the password with a secure alternative. As the name implies it is not necessary to enter a password anymore while authenticating against Microsoft 365/Azure AD.
What are the benefits?
- Increased security. Reduce the risk of password spray attacks by removing passwords as an attack surface.
- Better user experience. Provide easy access to applications and services such as Outlook, OneDrive, or Office while mobile.
- Robust insights. Gain insights into users passwordless activity with robust logging and auditing.
What are the current possible passwordless authentication methods?
- Windows Hello for Business is best for users on their dedicated Windows computers.
- Security keys is especially useful for users who sign in to shared machines like kiosks, in situations where use of phones is restricted, and for highly privileged identities.
- Microsoft Authenticator app is useful for providing a passwordless option to users with mobile devices. The Authenticator app turns any iOS or Android phone into a strong, passwordless credential by allowing users to sign into any platform or browser. Users sign in by getting a notification to their phone, matching a number displayed on the screen to the one on their phone, and then using their biometric data or PIN to confirm.
In this article we explore how-to incorporate the new passwordless authentication method in Azure AD using the Microsoft Authenticator app for a single user account.
Prerequisites
Before we can proceed with the actual setup of the phone sign-in with the Microsoft Authentication app, the following prerequisites must be met:
- You must be a Global Administrator to manage MFA in Microsoft 365 / Azure AD.
- Modern authentication must be enabled for your organization in Microsoft 365.
- Azure AD Multi-Factor Authentication enabled, with push notifications allowed as a verification method.
- Latest version of Microsoft Authenticator installed on a device running iOS or Android.
- At least an Azure AD P1 license in your tenant.
Associate Microsoft Authenticator with the Azure AD user account
The first step is to register the Microsoft Authenticator app to the test user account.
| # | Description | Screenshot |
| 1 | Open a browser and navigate to “mysignins.microsoft.com/security-info”.
You may need to login if you have not already. |
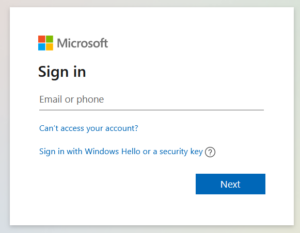 |
| 2 | Click on “Add method”. | 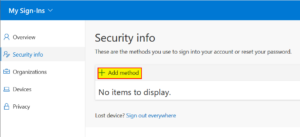 |
| 3 | Choose “Authenticator app” and click on “Add”.
If you don’t see this choice, you will need to enable it in the Azure AD settings. |
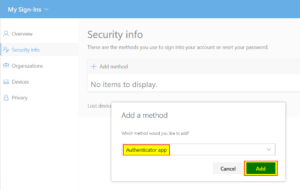 |
| 4 | You will need to download the Microsoft Authenticator app on your mobile phone before proceeding.
Click “Next”. |
 |
| 5 | Click “Next”. | 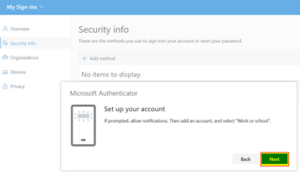 |
| 6 | Now open the Microsoft Authenticator app on the mobile phone and click on “+” sign. | 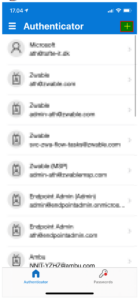 |
| 7 | Click on “Work or school account”. | 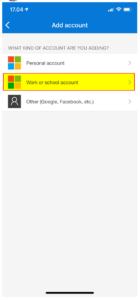 |
| 8 | Then click on “Scan QR code”. | 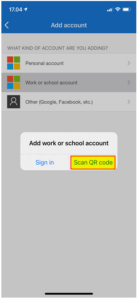 |
| 9 | Scan the QR-code on the computer screen with the mobile phone. | 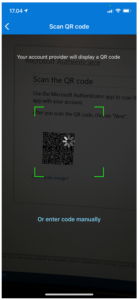 |
| 10 | Now back on the web browser on your computer, click “Next” | 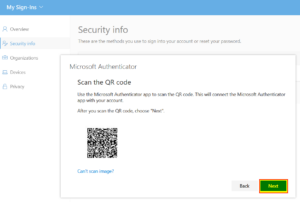 |
| 11 | On the mobile phone in the app, click “Approve”. | 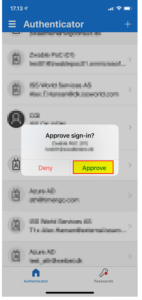 |
| 12 | In the web browser on the computer, click on “Next”. | 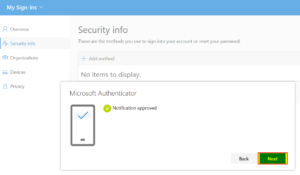 |
| 13 | The association is now complete. | 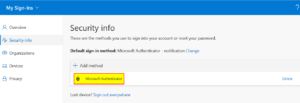 |
Enable passwordless phone sign-in authentication method in Azure AD
During login, the user can choose which authentication methods can be used. In this step we will enable Microsoft Authenticator. Before proceeding, make sure that you are Global Administrator.
| # | Description | Screenshot |
| 1 | Open a browser and navigate to “aad.portal.azure.com”.
You may need to login if you have not already. |
 |
| 2 | Click on “Azure Active Directory” and then on “Security”. | 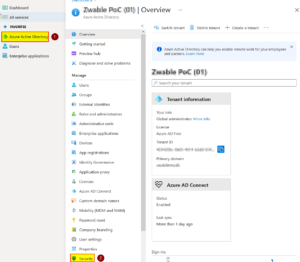 |
| 3 | Click on “Authentication methods” | 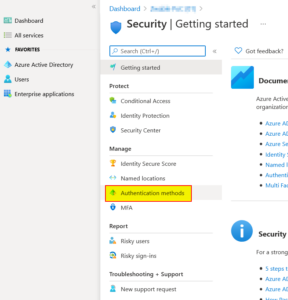 |
| 4 | If you haven’t enabled the combined security info registration experience, please do so.
Click on “Microsoft Authenticator”. |
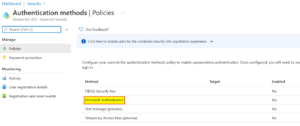 |
| 5 | Toggle “Enable” to “Yes” and choose “Selected users” and find the test user/group account you want to enable passwordless authentication on. | 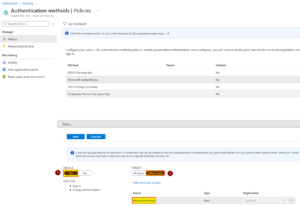 |
| 6 | By default, users are enabled to use Microsoft Authenticator in both passwordless and push notification modes called “Any” mode.
Passwordless: User must choose the correct answer in the app.
Push notification: User must approve login in the app.
You can choose which setting by clicking on the three dots and then click on “Configure”, otherwise skip to step 8. |
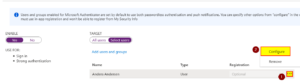 |
| 7 | Choose the desired mode and click on “Done”. | 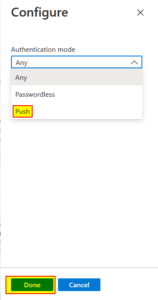 |
| 8 | Now click “Save”.
At may take a while to take effect on the user, in my lab it took up to 5-10 minutes. |
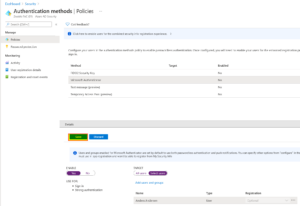 |
Enable phone sign-in in Microsoft Authenticator
The final step of the setup is to enable the Microsoft Authenticator on the phone to allow phone sign-in.
| # | Description | Screenshot |
| 1 | Open Microsoft Authenticator on your phone and then choose the association of the user account. | 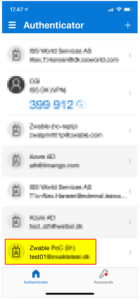 |
| 2 | Click on “Enable phone sign-in”. | 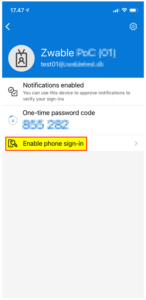 |
| 3 | Click on “Continue”. | 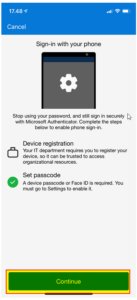 |
| 4 | Type your password and click on “Sign in”. | 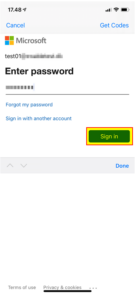 |
| 5 | The following action will register the device with Azure AD. Click on “Register” | 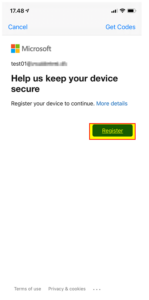 |
| 6 | Your device is now successfully registered, and you can login without a password. |  |
Test the passwordless authentication
If everything is setup correctly, we are now able to test the passwordless authentication method for our test user.
| # | Description | Screenshot |
| 1 | Open a new browser (remember to clear the cache) and navigate to portal.office.com and type in the user account. | 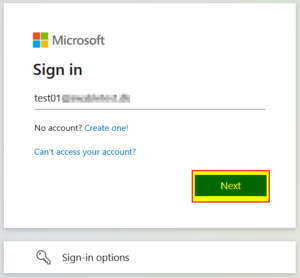 |
| 2 | You should now have the option “Use an app instead”. | 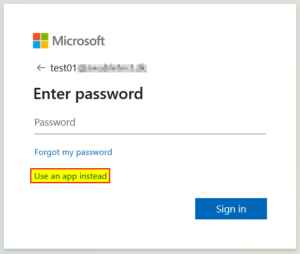 |
| 3 | A number “56” is shown on the screen in this example. |  |
| 4 | Now go to the Microsoft Authenticator app on your phone and select the number “56” matching on the screen. | 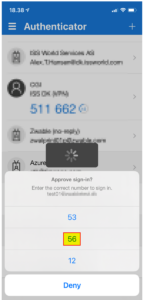 |
| 5 | You have now logged in without any password! |  |
Video
Final thoughts
Personally, I prefer passwordless over the traditional MFA method. During a day I write my password several times a day, this saves me a good amount of time by going passwordless.
If you prefer to setup through code, it is available through Microsoft Graph API (beta). For more information on the API endpoints, click here.
Currently it is only possible to enable phone sign-in with a single account per Microsoft Authenticator, this limits the usage. I have multiple accounts registered in Microsoft Authenticator on my mobile phone, but I am only able to choose one account for phone sign-in.
In my lab tests it took a good 5-10 minutes before settings was in effect, sometimes I needed to disable and then re-enable the authentication method in the Azure AD portal. My guess is that it needs to propagate to all Microsoft 365 regions before it is available to the users. Be patient!
